A 12-step program to get your blog so’s it can go out in public again
…when last we left the hacked blog, it had managed to delete the phony users and admins, and the permalinkspam was gone.
Jump ahead to last week, when I noticed that my Google AdSense boxes were always full of creepy advertising for boner pills. I have been playing with all kinds of plug-ins lately, trying to find something that will work well to “mobilize” this site. I wondered if any of them had done something to my header, so I clicked on “View page source” to see …
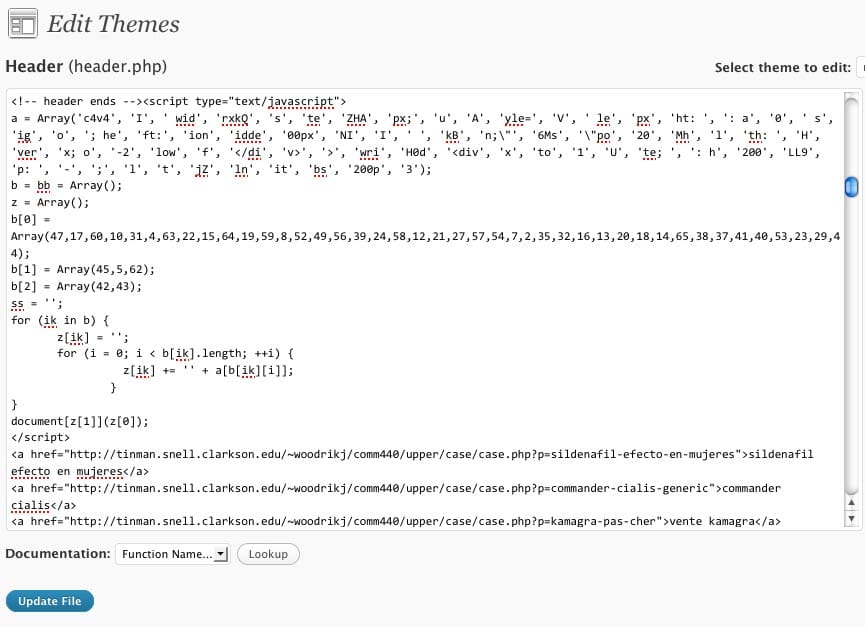
The list of links to sites underneath the noxious javascript ran for page after page. No woder my site loaded so sluggishy!
Great. Just great.
I know enough about Javascript to recognize when someone is being deliberately tricky about what they’re doing. The code in the window above uses the “Array” function, where all manner of short codes are stuffed in there to make nasty function calls and run a script that pulls in content and hides it out of sight in my header. This code then puts in the hypertext links such as the ones shown above (to some poor sap at a school whose computer is being used as a relay station for porno-pharma traffic).
Time to move to the next step in the program:
8. Made a list of all the plug-ins and started deleting them one by one
One of the really good rules for trying to fix something going heinously wrong on your computer is to start backtracking. Figure out what the last thing you did was, and try to undo it.
In this case, it was the plug-ins. I figured maybe someone had either gotten hacked, their plug-in was the way for a ‘sploit (hacker-speak for an “exploit” — a vulnerability in the software that they can worm their way through) to get into my scrupulously up-to-date blog. So I cacked all the plug-ins, and the next morning, opened up the Dashboard to find that the evil code was back in the header file.
9. No amends – only more evil code in the header
This happened two more times. It was time to start going through the PHP code line-by-line to try to figure out what the hell was going on. I used the editing tools that are integrated into the Dashboard on WordPress — to little avail.
I was starting to really wonder if the infection had reached the core PHP server, which would be epically bad news. I fired up my FTP program and started going through the library files. And there, I worked the next step:
10. I inventoried the files in the php-admin folder and admitted I had missed some pieces of the infection
I had to go through all the images for my blog postings, month by month, to find these little files. Even so, I damn near missed them – except that their edit dates were out of step with the dates that I uploaded the images.
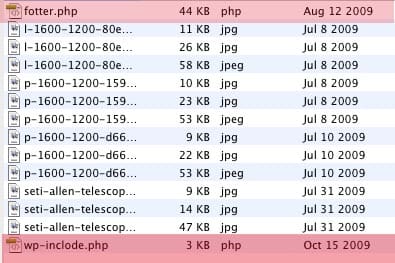
Deliberately misspelled -- but fiendishly close enough to actual words so that you might just miss them.
Check it out – they spelled “footer” as “fotter.php” so that it kinda blends in, but won’t break the blog. Like any good parasite, it knows that if it kills the host, then the blog won’t be up and functioning, and the little baby tapeworms won’t get to feast on the ill-gotten pharamaspam revenues that come from the links stuffed into my blog.
I also found a .gz file deep in a totally separate subdirectory under my wp-admin folder. I won’t show you the screengrab of that one, since it has some other identifying information in it. But again, as you look through all your folders and subdirectories, just keep an eye out for something that looks like it doesn’t belong. Think of the method that astroners use to find comets: they alternately flash big pictures of the sky, and look for the little dots that are strobing. Those are the points of light that are in slightly different positions from one frame to the next.
The problem also goes a bit deeper into some of the files on the PHP server; the links in the previous post will take you to pages that explain, far better than I could, how you can search for the vile infected strings of Javascript. Part of the problem is that they take advantage of a “reverse” function – where the commands are spelled out backwards, and then the server is instructed to read them that way. It looks again like gibberish to human eyes, but to a machine, it means “Stuff the trojans in here!”
Look for files that are wildly differing in size than they should be. If you do open them up, do it in a Text reader – not a Word document. Word probably won’t execute the Java code if it’s just pasted into a page as pure text, but man, with this stuff, it pays to be careful.
11. Prayed and meditated that I had at long last, cleansed the scourge from my blog
At this point, I’ve spent more than three days in all, fine-tooth-combing my blog and all the associated PHP, HTML and image files, folders, subcategories and god knows what all. I’m beat. Either I’ve gotten it or I haven’t, and it’s time to call in someone who is better at this than me.
And then on Sunday – I opened up the blog in my browser and hit “Page Source” … CLEAN!
And now for the last step (and I have tried to keep these steps at least vaguely in line with the instructions for AA and other 12-step programs):
12. Having had a blogging awakening, I try to carry this message to other bloggers, and practice the following principles with all my WordPress installs
I hope you’ve managed to get some learnings out of this strange screed. I know the presentation has been a bit quirky, and to be honest, about halfway through I realized I was pretty much beating the metaphorical dead horse into goo. But the point of all this is that I could have avoided all this pain, not had about 6 months of blog postings tainted and probably really awful Google page-rankings, if I had just kept the site properly updated.
When WordPress or other software does a critical release – for God’s sake, download and update it. The thing is, when they do a major release and bugfix, they have to publish exactly what bugs they are fixing. Which is like a paint-by-numbers for the hackers out there. They know exactly where and what the hole in the software was, and can start churning out botcode to take advantage of updating sluggards (like me).
Well, I have seen the light. no more slacking off on updating – and no more willy-nilly experimentation with fancy plugins on a site that I use for my business.
